Nmap 5.50
A primary focus of this release is the Nmap Scripting Engine, which has allowed Nmap to expand up the protocol stack and take network discovery to the next level. Nmap can now query all sorts of application protocols, including web servers, databases, DNS servers,FTP, and now even Gopher servers! Remember those? These capabilities are in self-contained libraries and scripts to avoid bloating Nmap's core engine.

inSSIDer
inSSIDer 2 will display all Wi-Fi access points within range and display their MAC address, SSID, RSSI, Channel, Vendor, Encryption, Max Rate and Network Type. Use the filters feature to quickly sort through long lists of access points. Great news for Linux users! inSSIDer 2, a very popular free/open source Wi-Fi network scanner for Windows Vista and Windows XP is now available for Linux Download inSSIDer 2 for Linux (currently alpha) - includes .deb and .rpm.

SuperTuxKart
It’s here, racing fans – a brand new version of iconic Linux game ‘SuperTuxKart’ is now available for download.

Install VirtualBox 4.0 (Stable) In Ubuntu, Via Repository
VirtualBox 4.0 has been released today. We've already covered what's new in VirtualBox 4.0 when the first beta came out so check out that post or the changelog for more info. As you probably know, starting with VirtualBox 4.0 some features are now available separately, in an extension pack. Here are the step-by-step instructions on installing both VirtualBox and the Extensions Pack in Ubuntu.

Friday, September 12, 2008
Google Chrome (BETA) for Windows
 4:17 PM
4:17 PM
 fog flames
fog flames
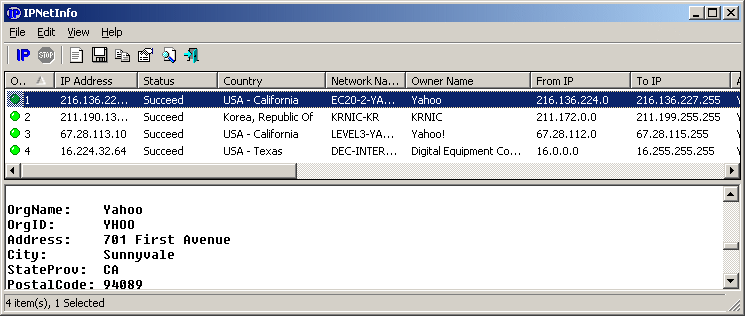
IPNetInfo v1.16 - Retrieves IP Address Information
 3:53 PM
3:53 PM
 fog flames
fog flames
Wednesday, September 10, 2008
Acunetix Web Vulnerability Scanner
 4:51 PM
4:51 PM
 fog flames
fog flames
- Websites and related web applications must be available 24 x 7 to provide the required service to customers, employees, suppliers and other stakeholders
- Firewalls and SSL provide no protection against web application hacking, simply because access to the website has to be made public
- Web applications often have direct access to backend data such as customer databases and, hence, control valuable data and are much more difficult to secure
- Custom applications are more susceptible to attack because they involve a lesser degree of testing than off-the-shelf software
- Hackers prefer gaining access to the sensitive data because of the immense pay-offs in selling the data.
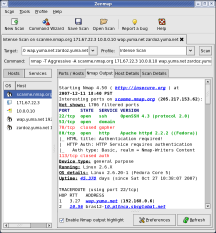
Zenmap
 4:41 PM
4:41 PM
 fog flames
fog flames
L0phtcrack
 4:33 PM
4:33 PM
 fog flames
fog flames

| L0phtcrack : Windows password auditing and recovery application L0phtCrack, also known as LC5, attempts to crack Windows passwords from hashes which it can obtain (given proper access) from stand-alone Windows NT/2000 workstations, networked servers, primary domain controllers, or Active Directory. In some cases it can sniff the hashes off the wire. It also has numerous methods of generating password guesses (dictionary, brute force, etc). LC5 was discontinued by Symantec in 2006, but you can still find the LC5 installer floating around. The free trial only lasts 15 days, and Symantec won't sell you a key, so you'll either have to cease using it or find a key generator. Since it is no longer maintained, you are probably better off trying Cain and Abel, John the Ripper, or Ophcrack instead. |
THC Hydra
 4:28 PM
4:28 PM
 fog flames
fog flames

| THC Hydra : A Fast network authentication cracker which support many different services. When you need to brute force crack a remote authentication service, Hydra is often the tool of choice. It can perform rapid dictionary attacks against more then 30 protocols, including telnet, ftp, http, https, smb, several databases, and much more. Like THC Amap this release is from the fine folks at THC. |
Thursday, September 4, 2008
John the Ripper
 4:53 PM
4:53 PM
 fog flames
fog flames

Wednesday, September 3, 2008
Preventing SQL Injection Attacks
 5:06 PM
5:06 PM
 fog flames
fog flames
In a previous article we provided some examples of how intruders will try to attack your site using Cross-site Scripting (XSS) attacks. In an XSS attack, the attacker tries to use client-side methods of injecting client-side script and then high-jacking a user's session. Now, we're going to provide some examples of a server-side attack where an intruder will try to obtain information from within your database. After the examples, we will go through methods of securing your code against these types of attacks.
SQL injection attacks take advantage of code that does not filter input that is being entered directly into a form. Susceptible applications are applications that take direct user input and then generate dynamic SQL that is executed via back-end code. For example say you have a logon form that accepts a user name and password. Once authenticated against the database, the application then sets a session value, or some other token for allowing the user to access the protected data.
Take a logon form for example, here you have two basic form elements, a textbox for accepting a user name, and a password box for the password.
Then in the code behind:
Dim SQL As String = "SELECT Count(*) FROM Users WHERE UserName = '" & _
username.text & "' AND Password = '" & password.text & "'"
Dim thisCommand As SQLCommand = New SQLCommand(SQL, Connection)
Dim thisCount As Integer = thisCommand.ExecuteScalar()
In the previous code block it executes the built SQL script directly, if count is greater than one, then you know the values entered in for the user name and password were the ones matching the database.
Now with that code in the previous example, suppose someone entered the following string into your username text box:
' or 0=0 --
The apostrophe will close the username value being sent to the SQL query, then pass another argument to the SQL query, after the last argument it then comments out the rest of the query using the "--". Since the second argument they entered into your texbox is an "or" statement, the first check on the user name doesn't matter, and since 0 is always going to equal 0 the script will execute successfully and return a positive logon. Guess what? Your intruder now has access to your application.
Ok so maybe they can logon into your application, but what else can they do? Let's take another example of SQL injection, as in the previous example of using the apostrophe to terminate the value, and proceed on to another argument, lets do this, but using something that can really ruin your application's data and day:
'; drop table users --
Definitely something that can ruin your day. Of course this type of an attack you'll probably notice pretty quick. Other SQL commands can then be entered to determine your database's structure, and return all user names and passwords from the database. You make it even easier for the attacker if you do not provide some ambiguous error message and provide the error message returned from .NET. This error message can provide critical information they need to determine what to enter in your form in order to obtain information.
SQL Injection Prevention
One method of preventing SQL injection is to avoid the use of dynamically generated SQL in your code. By using parameterized queries and stored procedures, you then make it impossible for SQL injection to occur against your application. For example, the previous SQL query could have been done in the following way in order to avoid the attack demonstrated in the example:
Dim thisCommand As SQLCommand = New SQLCommand("SELECT Count(*) " & _
"FROM Users WHERE UserName = @username AND Password = @password", Connection)
thisCommand.Parameters.Add ("@username", SqlDbType.VarChar).Value = username
thisCommand.Parameters.Add ("@password", SqlDbType.VarChar).Value = password
Dim thisCount As Integer = thisCommand.ExecuteScalar()
By passing parameters you avoid many types of SQL injection attacks, and even better method of securing your database access is to use stored procedures. Stored procedures can secure your database by restricting objects within the database to specific accounts, and permitting the accounts to just execute stored procedures. Your code then does all database access using this one account that only has access to execute stored procedures. You do not provide this account any other permissions, such as write, which would allow an attacker to enter in SQL statement to executed against your database. Any interaction to your database would have to be done using a stored procedure which you wrote and is in the database itself, which is usually inaccessible to a perimeter network or DMZ.
So if you wanted to do the authentication via a stored procedure, it may look like the following:
Dim thisCommand As SQLCommand = New SqlCommand ("proc_CheckLogon", Connection)
thisCommand.CommandType = CommandType.StoredProcedure
thisCommand.Parameters.Add ("@username", SqlDbType.VarChar).Value = username
thisCommand.Parameters.Add ("@password", SqlDbType.VarChar).Value = password
thisCommand.Parameters.Add ("@return", SqlDbType.Int).Direction = ParameterDirection.ReturnValue
Dim thisCount As Integer = thisCommand.ExecuteScalar()
Finally, ensure you provide very little information to the user when an error does occur. If there is database access failure, make sure you don't dump out the entire error message. Always try to provide the least amount of information possible to the users. Besides, do you want them to start helping you to debug your code? If not, why provide them with debugging information?
By following these tips for your database access you're on your way to preventing unwanted eyes from viewing your data.
By: Patrick Santry, Microsoft MVP (ASP/ASP.NET), developer of this site, author of books on Web technologies, and member of the DotNetNuke core development team. If you're interested in the services provided by Patrick, visit his company Website at Santry.com.
Tuesday, September 2, 2008
Crack Windows Password With Back|track
 4:15 PM
4:15 PM
 fog flames
fog flames

It's evolved from the merge of the two wide spread distributions - Whax and Auditor Security Collection. By joining forces and replacing these distributions, BackTrack has gained massive popularity and was voted in 2006 as the #1 Security Live Distribution by insecure.org. Security professionals as well as new comers are using BackTrack as their favorite toolset all over the globe.
BackTrack has a long history and was based on many different linux distributions until it is now based on a Slackware linux distribution and the corresponding live-CD scripts by Tomas M. (www.slax.org) . Every package, kernel configuration and script is optimized to be used by security penetration testers. Patches and automation have been added, applied or developed to provide a neat and ready-to-go environment.
After coming into a stable development procedure during the last releases and consolidating feedbacks and addition, the team was focused to support more and newer hardware as well as provide more flexibility and modularity by restructuring the build and maintenance processes. With the current version, most applications are built as individual modules which help to speed up the maintenance releases and fixes.
Because Metasploit is one of the key tools for most analysts it is tightly integrated into BackTrack and both projects collaborate together to always provide an on-the-edge implementation of Metasploit within the BackTrack CD-Rom images or the upcoming remote-exploit.org distributed and maintained virtualization images (like VMWare images appliances).
Being superior while staying easy to use is key to a good security live cd. We took things a step further and aligned BackTrack to penetration testing methodologies and assessment frameworks (ISSAF and OSSTMM). This will help our professional users during their daily reporting nightmares.
Currently BackTrack consists of more than 300 different up-to-date tools which are logically structured according to the work flow of security professionals. This structure allows even newcomers to find the related tools to a certain task to be accomplished. New technologies and testing techniques are merged into BackTrack as soon as possible to keep it up-to-date From : Remote-Exploit.
Now we Crack Windows Password With Back|track.
Step one boot with cd backtrack and login:
User : root
Password : toor
and open terminal with command :
bt~# mount
this command for check windows partation.. backtrack can read windows partation or not

and now look line 5 [ /dev/hda1 on /mnt/hda1 type ntfs (ro, noatime) ]
the meaning is, partation NTFS has been mount to directory /mnt/hda1 and now we cant acces windows file
with backtrack. this partation has mount with acces "read only" [ro] the meaning...we cannot change or
write in this directory.
and now we acces password windows directory [ \WINDOWS\system32\config\ ]
bt~# ls -l /mnt/hda1/WINDOWS/system32/config/sam
 and now our mission to got syskey! for got this syskey we can use bkhive program.
and now our mission to got syskey! for got this syskey we can use bkhive program.bt~# bkhive /mnt/hda1/WINDOWS/system32/config/system my_syskey

bt~# ls -l

windows has put password in sam file....this password has been encrypt with windows system
and now we try to got hash from windows sam file
what program we use? we can use "samdump2"....this program has been packed in backtrack
bt~# samdump2 /mnt/hda1/WINDOWS/system32/config/sam my_syskey

look this screen shot.... we got the hash value from windows password...
and we must crack again with program ophcrack aor john the Ripper.. on this case im use a john the Ripper for cracking :)
first we must save the password hash to txt file.. with command:
bt~# samdump2 /mnt/hda1/WINDOWS/system32/config/sam my_syskey > hash.txt
bt~# ls -l
and now has save the hash in txt file with name "hash.txt"
Now John the Ripper ready to cracking...
bt~# /pentest/password/Jhon-1.7.2/run/John hash.txt

bt~# /pentest/password/Jhon-1.7.2/run/John.pot

oops the password found [ POTONGAN ]... but i dont understand why John the Ripper separated
the end alphabet [ N ]
but we can show the password again with command:
bt~# /pentest/password/Jhon-1.7.2/run/John --show hash.txt

done...happy cracking :) and sorry about my bad engglish !